In my last blog post, we looked at the
Data Discovery & Classification features within the Advanced Data Security (ADS) offering for Azure SQL. In this blog post, we will have a look into Vulnerability assessment.
Azure SQL Overview
Azure SQL Database is a fully managed Platform as a Service (PaaS) Database Engine that handles most of the database management functions such as upgrading, patching, backups, and monitoring without user involvement. As with any database platform, security remains a top concern to address this issue or concerns Microsoft have offering called Advanced Data Security with Azure SQL service.
Pre-requisites
- Enable Advanced Data Security (ADS) at the database level by navigating to Settings > Advanced Data Security for your SQL database and click Enable.
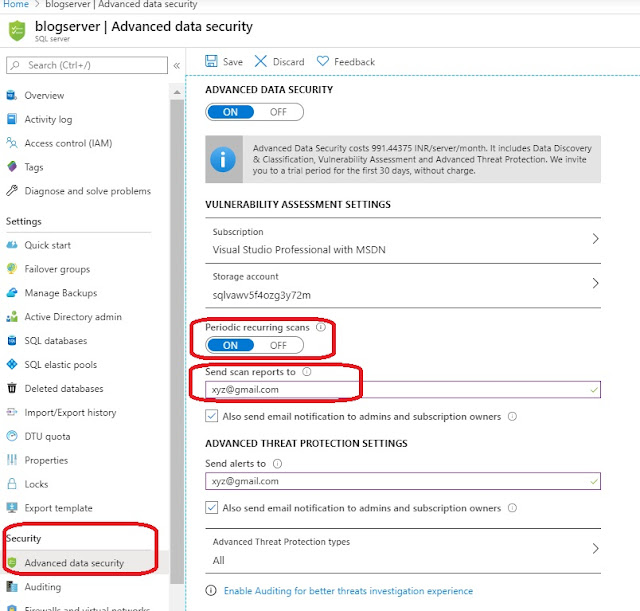
- Alternatively, ADS can also be configured and managed at the server level by navigating to Settings > Advanced Data Security for your server and switching the ‘Advanced Data Security’ setting from ‘Off’ to ‘On’.
Vulnerability Assessment
SQL Vulnerability Assessment is an easy-to-configure service that can discover, track, and help you remediate potential database vulnerabilities. The Vulnerability Assessment is a scanning service that contains a set of built-in rules based off Microsoft’s best practices with security. The scan contains 47 total security checks and will apply a risk-based on the individual check. This assessment should not be the only security measure for your database.
Vulnerability Assessment Configure
In order to run the Vulnerability Assessment, ADS must be enabled as described in pre-requisites. Storage account will be used to store results of the vulnerability scans with additional configuration like periodic scans, email report etc which are configured at Database server level as shown below.
To view the Vulnerability Assessment report navigate to Advanced data security > Vulnerability Assessment card.
Once a scan is run, the results are automatically displayed within the Azure portal. Report comprises of overview of your security state with a breakdown of how many have passed and failed security assessment with corresponding Risk level. Clicking on an individual security check will provide additional details and remediation procedure
However you will be able to decide whether the result is an acceptable baseline within your environment or whether remediation is required. If the result is acceptable, you can click the ‘Approve as Baseline’ button. It will no longer appear as a failure in your Vulnerability Assessment after your next scan.
You can easily export a copy of the report by clicking the ‘Export Scan Results’ button
References






Comments
Post a Comment